Questões da Prova Quadrix - 2014 - DATAPREV - Analista Tecnologia da Informação
Foram encontradas 50 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
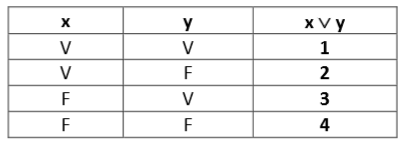
Essa tabela-verdade representa o funcionamento de 2 sensores x e y em um equipamento, de tal forma que:
V = VERDADEIRO, ou seja, o sensor está acionado.
F = FALSO, ou seja, o sensor não está acionado.
Assinale a alternativa que contém os valores CORRETOS para 1, 2, 3 e 4, considerando-se o Conectivo do tipo OU (x ∨ y).

Considering all the pronouns shown in the comic strip, we could say that:

According to the strip:
Self-repairing software tackles malware
University of Utah computer scientists have developed software that not only detects and eradicates never-before-seen viruses and other malware, but also automatically repairs damage caused by them. The software then prevents the invader from ever infecting the computer
again.
A3 is a software suite that works with a virtual machine - a virtual computer that emulates the operations of a computer without dedicated hardware. The A3 software is designed to watch over the virtual machine's operating system and applications, says Eric Eide, University of Utah research assistant professor of computer science leading the university's A3 team with U computer science associate professor John Regehr. A3 is designed to protect servers or similar business-grade computers that run on the Linux operating system. It also has been demonstrated to protect military applications.
The new software called A3, or Advanced Adaptive Applications, was co-developed by Massachusetts-based defense contractor, Raytheon BBN. The four-year project was completed in late September.
There are no plans to adapt A3 for home computers or laptops, but Eide says this could be possible in the future.
"A3 technologies could find their way into consumer products someday, which would help consumer devices protect themselves against fast-spreading malware or internal corruption of software components. But we haven't tried those experiments yet," he says.
Unlike a normal virus scanner on consumer PCs that compares a catalog of known viruses to something that has infected the computer, A3 can detect new, unknown viruses or malware automatically by sensing that something is occurring in the computer's operation that is not correct. It then can stop the virus, approximate a repair for the damaged software code, and then learn to never let that bug enter the machine gain.
While the military has an interest in A3 to enhance cybersecurity for its mission-critical systems, A3 also potentially could be used in the consumer space, such as in web services like Amazon. If a virus or attack stops the service, A3 could repair it in minutes without having to take the servers down.
Source: http://www.sciencedaily.com
"[...]computer scientists have developed software that not only detects and eradicates never-before-seen viruses and other malware, but also automatically repairs damage caused by them".
The words underlined express a meaning of: